

In today’s security-conscious world, high-security workplaces face the constant challenge of balancing accessibility with stringent safety measures. Visitor management systems have emerged as a crucial tool in enhancing access control while streamlining the visitor experience. Let’s explore how these innovative solutions are reshaping security protocols in sensitive environments by aiding to fortify defenses against unauthorized access and other security threats.
A visitor management system is a comprehensive software solution designed to track, manage, and monitor visitors entering a facility. These systems replace traditional paper logbooks with digital platforms that offer a range of advanced features, from pre-registration to real-time monitoring. The key components of a digital visitor management system include:
High-security workplaces, such as government facilities, data centers, research laboratories, and financial institutions, require robust access control measures to protect sensitive information, physical assets, secure areas, and personnel. Traditional methods often fall short of providing the level of security and protection needed in these environments, compromising the confidentiality of the environment.
Bolstering the access control strategies in high-security settings is essential to address these vulnerabilities and elevate overall security. Advanced systems, such as multi-factor authentication, and integrated visitor access management platforms offer improved accuracy and reliability. These technologies provide the relevant functionalities to overcome the multiple challenges that can be observed with regard to maintaining site security in such workplaces.
Boost your food business’s hygiene standards with Smart Food Safe’s tech-driven solutions—streamline 4C processes to yield optimal results, and ensure compliance effortlessly.

Boost your food business’s hygiene standards with Smart Food Safe’s tech-driven solutions—streamline 4C processes to yield optimal results, and ensure compliance effortlessly.
Common challenges faced by high-security workplaces include, but are not limited to:
In the absence of proper visitor identity verification procedures for an enterprise or weak authentication methods, it can result in failure to meet security regulations.
Impact – Inadequate identity verification increases the risk of allowing unauthorized or potentially harmful individuals into secure areas, compromising the site security protocols.
Dealing with manual visitor check-in processes can be troublesome for businesses as it involves paper logs or outdated systems, which are often slow and prone to errors.
Impact – These manual processes can result in delays, inaccuracies in visitor records, and increased risk of security lapses due to human error, affecting operational efficiency and security.
Ensuring that unauthorized individuals do not gain access to restricted or secure areas is a significant challenge for enterprises.
Impact – Unauthorized access due to inadequate measures or lapses in visitor verification can lead to security breaches, theft, data loss, or potential harm to personnel. It undermines the integrity of security protocols and increases the risk of internal and external threats.
Enterprises often struggle with smoothly processing large volumes of visitors, especially during peak times or major events. This challenge includes managing visitor check-ins and ensuring timely access control while maintaining accurate visitor records.
Impact – Tedious visitor processing can lead to long wait times, increased congestion at entry points, and potential security risks due to rushed or incomplete checks negatively affecting the overall visitor experience and security management.
Many enterprises struggle with inadequate systems for tracking and recording visitor movements and activities. This often results in incomplete or unreliable visitor logs.
Impact – Ineffective visitor tracking can impede incident investigations, complicate compliance with security standards, and diminish accountability, ultimately leading to security vulnerabilities.
The lack of mechanisms for enforcing industry-specific regulations that ensure the safety of the site throughout the visitor cycle can bring forth several security risks.
Impact – Poor compliance with industry regulations can lead to safety risks, legal liabilities, financial losses, reputational damage, and operational disruptions, ultimately threatening the organization’s viability and visitor trust.
Visitor management systems have become indispensable tools for improving access control in high-security workplaces. By leveraging advanced technologies and systematic processes, these systems boost security, improve efficiency, and provide a better experience for both visitors and staff.
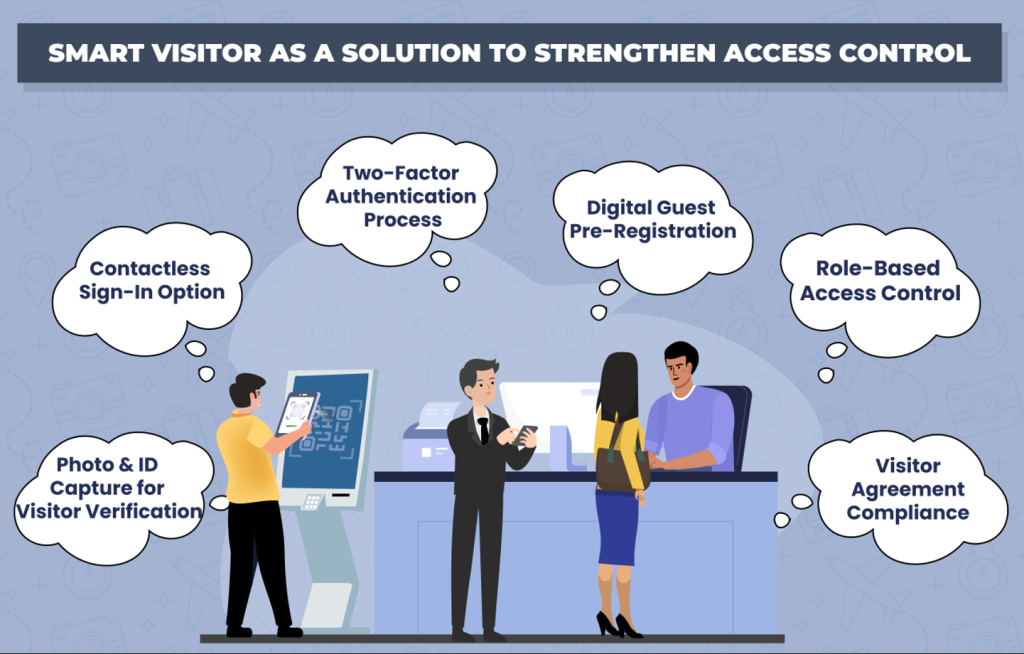
Visitor management systems employ cutting-edge technologies to verify visitor identities with unprecedented accuracy. By integrating ID scanning capabilities, these systems can quickly cross-reference government-issued identification against watchlists and internal databases.
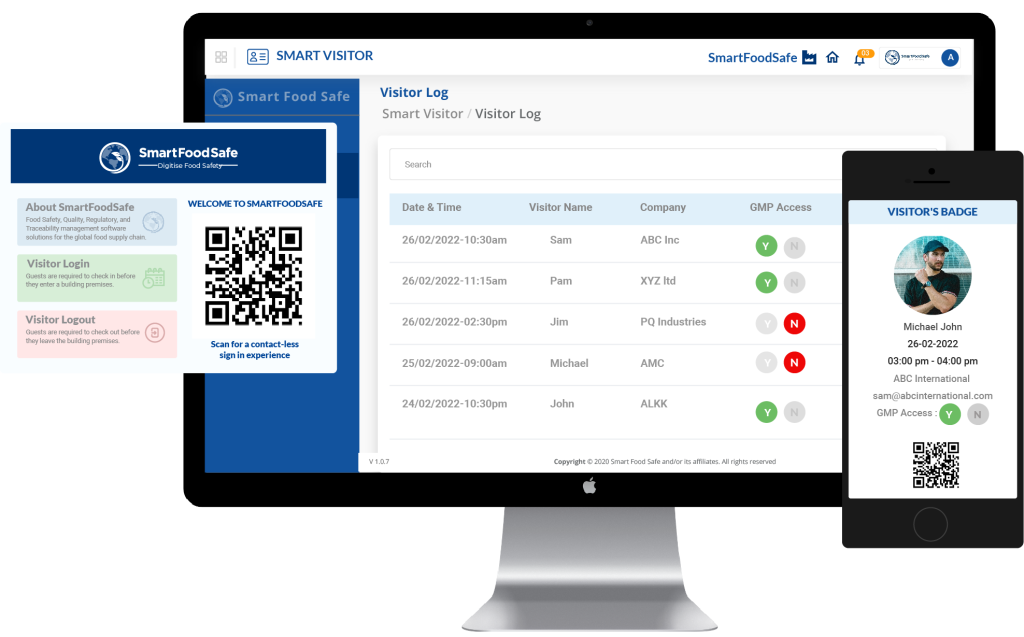
In response to the growing demand for convenience and safety, visitor management systems now offer contactless check-in options. Features such as QR code check-ins, facial recognition, and mobile check-in applications minimize physical contact while maintaining high-security standards. This not only refines the visitor experience but also aligns with modern health and safety protocols.
One of the key advantages of visitor management systems is their ability to offer customizable security protocols as the access can be controlled based on the specific needs of different areas within a facility. Administrators can set up varying levels of access permissions, implement zone-based access control, and issue time-limited access passes. This ensures that visitors only enter authorized zones.
Visitor management systems address visitor volume issues by offering a pre-registration process, allowing visitors to register online before arrival. This significantly reduces check-in times, improves the overall visitor experience, and enhances security through advanced screening. The ability to process large volumes of visitors quickly and efficiently ensures that security measures are upheld even during busy periods.
Tracking and recording visitor movements is substantial as the wealth of data hence collected through visitor traffic pattern analysis can be utilized to identify security trends, optimize protocols, and make informed decisions about resource allocation. Visitor management systems provide detailed logs of every visitor’s activities, including entry and exit times, areas accessed, and duration of stay. Security personnel can access up-to-date information on who is in the building, their location, and the purpose of their visit.
Integrated visitor agreements within a visitor management system usher regulatory compliance by requiring visitors to acknowledge and adhere to industry-specific safety protocols before gaining access to the enterprise facilities. This approach ensures that all visitors are informed of and agree to the necessary regulations, thereby guaranteeing site safety through better enforcement of compliance standards.
As security threats continue to evolve, the role of visitor management systems in safeguarding sensitive environments will only grow in importance.
For organizations looking to revamp their security protocols and improvise visitor management, tech-assisted tools like Smart Visitor offer pioneering features tailored to the needs of high-security environments. By implementing Smart Visitor, businesses can confidently stay ahead of security challenges. We make it possible by equipping companies to tackle the various site-security challenges by incorporating the above-mentioned solutions to strengthen access control.
Smart Visitor stands as a trustworthy technology solution for visitor management in providing peace of mind for both visitors and staff at high-security workplaces.
Promote safety and confidence for visitors and staff at high-security workplaces with Smart Visitor.
In today’s security-conscious world, high-security workplaces face the constant challenge of balancing accessibility with stringent safety measures. Visitor management systems have emerged as a crucial tool in enhancing access control while streamlining the visitor experience. Let’s explore how these innovative solutions are reshaping security protocols in sensitive environments by aiding to fortify defenses against unauthorized access and other security threats.
A visitor management system is a comprehensive software solution designed to track, manage, and monitor visitors entering a facility. These systems replace traditional paper logbooks with digital platforms that offer a range of advanced features, from pre-registration to real-time monitoring. The key components of a digital visitor management system include:
High-security workplaces, such as government facilities, data centers, research laboratories, and financial institutions, require robust access control measures to protect sensitive information, physical assets, secure areas, and personnel. Traditional methods often fall short of providing the level of security and protection needed in these environments, compromising the confidentiality of the environment.
Bolstering the access control strategies in high-security settings is essential to address these vulnerabilities and elevate overall security. Advanced systems, such as multi-factor authentication, and integrated visitor access management platforms offer improved accuracy and reliability. These technologies provide the relevant functionalities to overcome the multiple challenges that can be observed with regard to maintaining site security in such workplaces.
Boost your food business’s hygiene standards with Smart Food Safe’s tech-driven solutions—streamline 4C processes to yield optimal results, and ensure compliance effortlessly.

Common challenges faced by high-security workplaces include, but are not limited to:
In the absence of proper visitor identity verification procedures for an enterprise or weak authentication methods, it can result in failure to meet security regulations.
Impact – Inadequate identity verification increases the risk of allowing unauthorized or potentially harmful individuals into secure areas, compromising the site security protocols.
Dealing with manual visitor check-in processes can be troublesome for businesses as it involves paper logs or outdated systems, which are often slow and prone to errors.
Impact – These manual processes can result in delays, inaccuracies in visitor records, and increased risk of security lapses due to human error, affecting operational efficiency and security.
Ensuring that unauthorized individuals do not gain access to restricted or secure areas is a significant challenge for enterprises.
Impact – Unauthorized access due to inadequate measures or lapses in visitor verification can lead to security breaches, theft, data loss, or potential harm to personnel. It undermines the integrity of security protocols and increases the risk of internal and external threats.
Enterprises often struggle with smoothly processing large volumes of visitors, especially during peak times or major events. This challenge includes managing visitor check-ins and ensuring timely access control while maintaining accurate visitor records.
Impact – Tedious visitor processing can lead to long wait times, increased congestion at entry points, and potential security risks due to rushed or incomplete checks negatively affecting the overall visitor experience and security management.
Many enterprises struggle with inadequate systems for tracking and recording visitor movements and activities. This often results in incomplete or unreliable visitor logs.
Impact – Ineffective visitor tracking can impede incident investigations, complicate compliance with security standards, and diminish accountability, ultimately leading to security vulnerabilities.
The lack of mechanisms for enforcing industry-specific regulations that ensure the safety of the site throughout the visitor cycle can bring forth several security risks.
Impact – Poor compliance with industry regulations can lead to safety risks, legal liabilities, financial losses, reputational damage, and operational disruptions, ultimately threatening the organization’s viability and visitor trust.
Visitor management systems have become indispensable tools for improving access control in high-security workplaces. By leveraging advanced technologies and systematic processes, these systems boost security, improve efficiency, and provide a better experience for both visitors and staff.
Visitor management systems employ cutting-edge technologies to verify visitor identities with unprecedented accuracy. By integrating ID scanning capabilities, these systems can quickly cross-reference government-issued identification against watchlists and internal databases.
In response to the growing demand for convenience and safety, visitor management systems now offer contactless check-in options. Features such as QR code check-ins, facial recognition, and mobile check-in applications minimize physical contact while maintaining high-security standards. This not only refines the visitor experience but also aligns with modern health and safety protocols.
One of the key advantages of visitor management systems is their ability to offer customizable security protocols as the access can be controlled based on the specific needs of different areas within a facility. Administrators can set up varying levels of access permissions, implement zone-based access control, and issue time-limited access passes. This ensures that visitors only enter authorized zones.
Visitor management systems address visitor volume issues by offering a pre-registration process, allowing visitors to register online before arrival. This significantly reduces check-in times, improves the overall visitor experience, and enhances security through advanced screening. The ability to process large volumes of visitors quickly and efficiently ensures that security measures are upheld even during busy periods.
Tracking and recording visitor movements is substantial as the wealth of data hence collected through visitor traffic pattern analysis can be utilized to identify security trends, optimize protocols, and make informed decisions about resource allocation. Visitor management systems provide detailed logs of every visitor’s activities, including entry and exit times, areas accessed, and duration of stay. Security personnel can access up-to-date information on who is in the building, their location, and the purpose of their visit.
Integrated visitor agreements within a visitor management system usher regulatory compliance by requiring visitors to acknowledge and adhere to industry-specific safety protocols before gaining access to the enterprise facilities. This approach ensures that all visitors are informed of and agree to the necessary regulations, thereby guaranteeing site safety through better enforcement of compliance standards.
As security threats continue to evolve, the role of visitor management systems in safeguarding sensitive environments will only grow in importance.
For organizations looking to revamp their security protocols and improvise visitor management, tech-assisted tools like Smart Visitor offer pioneering features tailored to the needs of high-security environments. By implementing Smart Visitor, businesses can confidently stay ahead of security challenges. We make it possible by equipping companies to tackle the various site-security challenges by incorporating the above-mentioned solutions to strengthen access control.
Smart Visitor stands as a trustworthy technology solution for visitor management in providing peace of mind for both visitors and staff at high-security workplaces.

Promote safety and confidence for visitors and staff at high-security workplaces with Smart Visitor.
Signup to receive latest news, insights and updates on Visitor management